How about a 21 year-old British college student from Liverpool named Joseph James Connor who is stranded in Spain due to Covid travel bans and based on preliminary evidence, appears to be the perpetrator. JL
Krebs on Security reports:
PlugWalkJoe in real life is a 21-year-old from Liverpool, U.K. named Joseph James Connor. PlugWalkJoe is in Spain where he was attending a university until earlier this year (but) has been unable to return home on account of travel restrictions due to the COVID-19 pandemic. It’s fitting that he was identified in part via social engineering. We should all be grateful the perpetrators of this attack on Twitter did not set their sights on disrupting an election or the stock market, or attempting to start a war by issuing false, inflammatory tweets from world leaders.
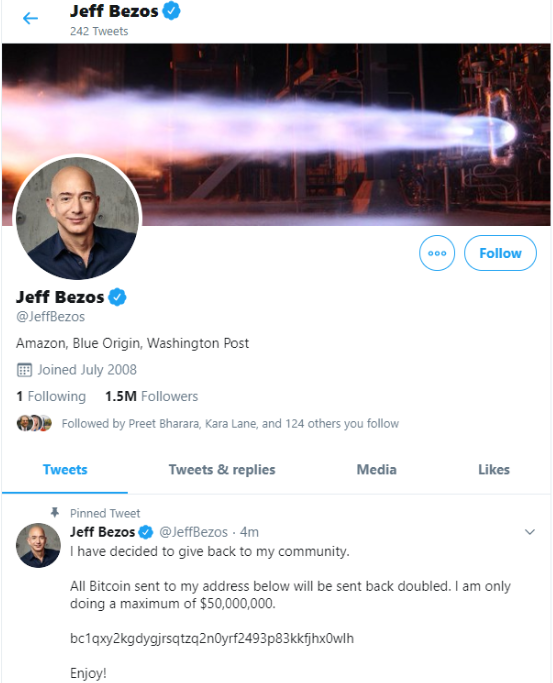
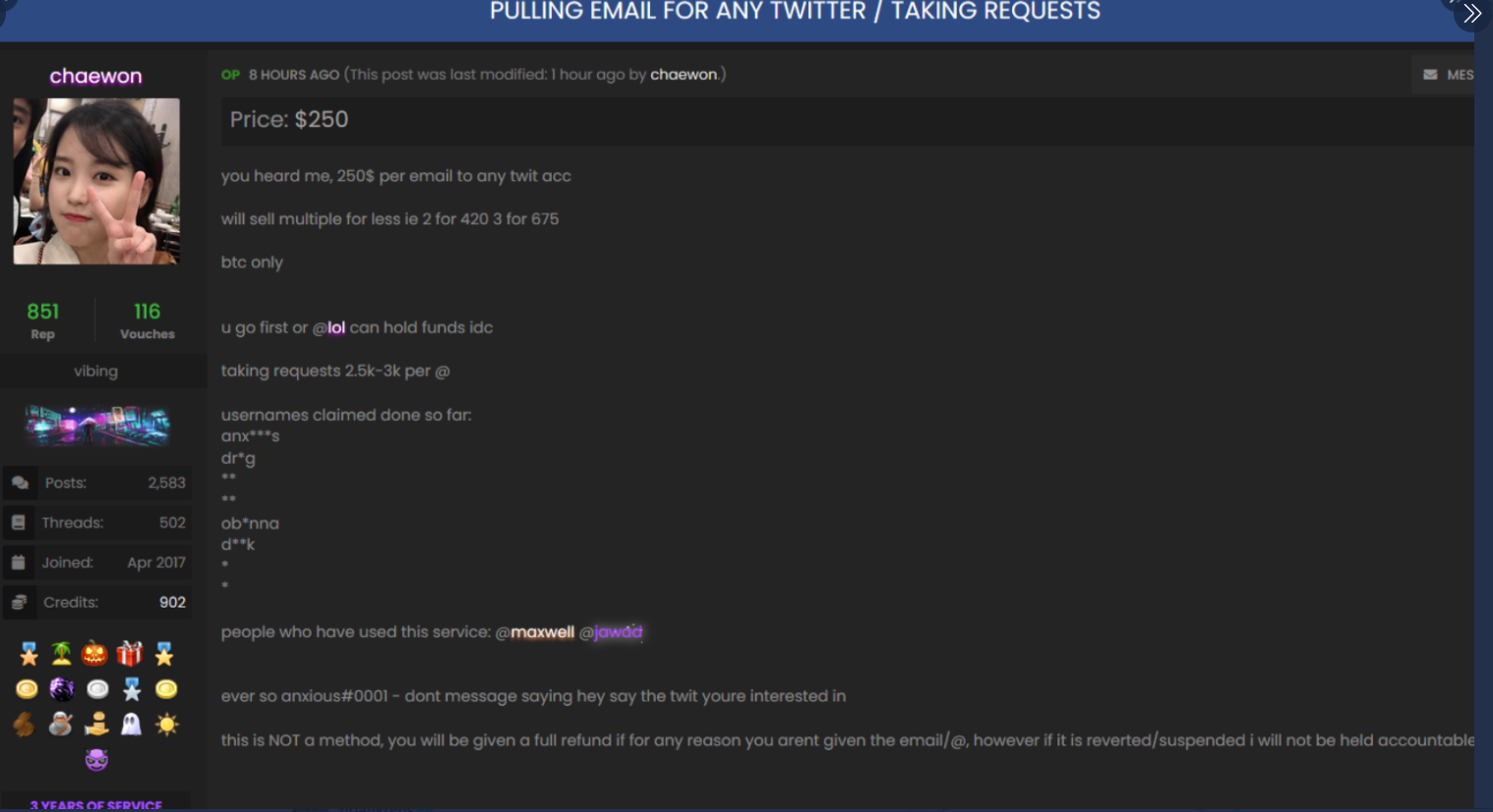
Twitter was thrown into chaos on Wednesday after accounts for some of the world’s most recognizable public figures, executives and celebrities starting tweeting out links to bitcoin scams. Twitter says the attack happened because someone tricked or coerced an employee into providing access to internal Twitter administrative tools. This post is an attempt to lay out some of the timeline of the attack, and point to clues about who may have been behind it.The first public signs of the intrusion came around 3 PM EDT, when the Twitter account for the cryptocurrency exchange Binance tweeted a message saying it had partnered with “CryptoForHealth” to give back 5000 bitcoin to the community, with a link where people could donate or send money.Minutes after that, similar tweets went out from the accounts of other cryptocurrency exchanges, and from the Twitter accounts for democratic presidential candidate Joe Biden, Amazon CEO Jeff Bezos, President Barack Obama, Tesla CEO Elon Musk, former New York Mayor Michael Bloomberg and investment mogul Warren Buffett.While it may sound ridiculous that anyone would be fooled into sending bitcoin in response to these tweets, an analysis of the BTC wallet promoted by many of the hacked Twitter profiles shows that over the past 24 hours the account has processed 383 transactions and received almost 13 bitcoin — or approximately USD $117,000.Twitter issued a statement saying it detected “a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools. We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”There are strong indications that this attack was perpetrated by individuals who’ve traditionally specialized in hijacking social media accounts via “SIM swapping,” an increasingly rampant form of crime that involves bribing, hacking or coercing employees at mobile phone and social media companies into providing access to a target’s account.People within the SIM swapping community are obsessed with hijacking so-called “OG” social media accounts. Short for “original gangster,” OG accounts typically are those with short profile names (such as @B or @joe). Possession of these OG accounts confers a measure of status and perceived influence and wealth in SIM swapping circles, as such accounts can often fetch thousands of dollars when resold in the underground.In the days leading up to Wednesday’s attack on Twitter, there were signs that some actors in the SIM swapping community were selling the ability to change an email address tied to any Twitter account. In a post on OGusers — a forum dedicated to account hijacking — a user named “Chaewon” advertised they could change email address tied to any Twitter account for $250, and provide direct access to accounts for between $2,000 and $3,000 apiece.
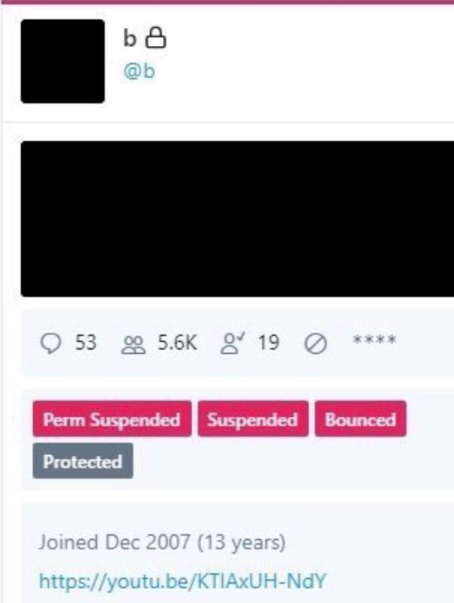
The OGUsers forum user “Chaewon” taking requests to modify the email address tied to any twitter account.“This is NOT a method, you will be given a full refund if for any reason you aren’t given the email/@, however if it is revered/suspended I will not be held accountable,” Chaewon wrote in their sales thread, which was titled “Pulling email for any Twitter/Taking Requests.”Hours before any of the Twitter accounts for cryptocurrency platforms or public figures began blasting out bitcoin scams on Wednesday, the attackers appear to have focused their attention on hijacking a handful of OG accounts, including “@6.”That Twitter account was formerly owned by Adrian Lamo — the now-deceased “homeless hacker” perhaps best known for breaking into the New York Times’s network and for reporting Chelsea Manning‘s theft of classified documents. @6 is now controlled by Lamo’s longtime friend, a security researcher and phone phreaker who asked to be identified in this story only by his Twitter nickname, “Lucky225.”Lucky225 said that just before 2 p.m. EDT on Wednesday, he received a password reset confirmation code via Google Voice for the @6 Twitter account. Lucky said he’d previously disabled SMS notifications as a means of receiving multi-factor codes from Twitter, opting instead to have one-time codes generated by a mobile authentication app.But because the attackers were able to change the email address tied to the @6 account and disable multi-factor authentication, the one-time authentication code was sent to both his Google Voice account and to the new email address added by the attackers.“The way the attack worked was that within Twitter’s admin tools, apparently you can update the email address of any Twitter user, and it does this without sending any kind of notification to the user,” Lucky told KrebsOnSecurity. “So [the attackers] could avoid detection by updating the email address on the account first, and then turning off 2FA.”Lucky said he hasn’t been able to review whether any tweets were sent from his account during the time it was hijacked because he still doesn’t have access to it (he has put together a breakdown of the entire episode at this Medium post).But around the same time @6 was hijacked, another OG account – @B — was swiped. Someone then began tweeting out pictures of Twitter’s internal tools panel showing the @B account.
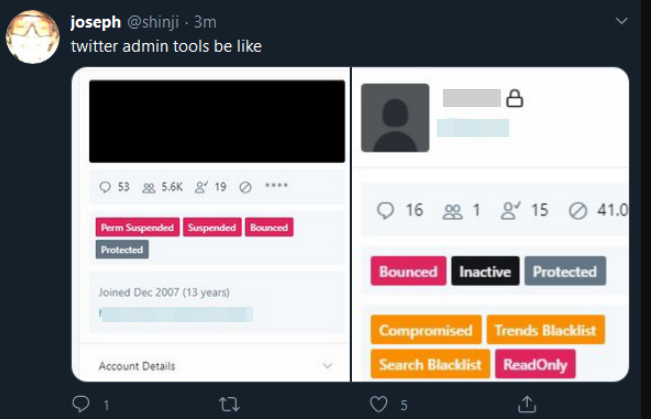
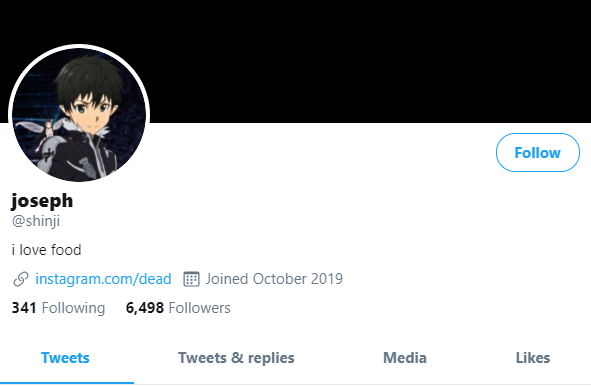
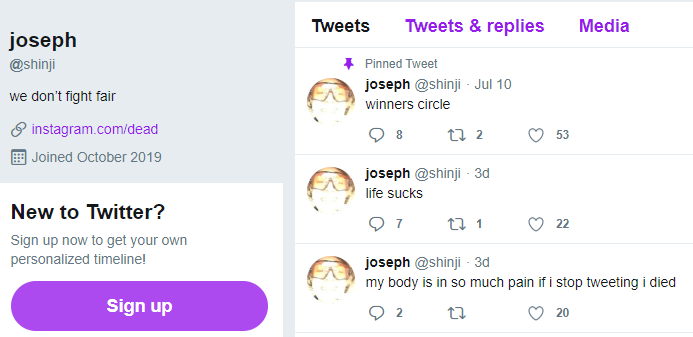
A screenshot of the hijacked OG Twitter account “@B,” shows the hijackers logged in to Twitter’s internal account tools interface.Twitter responded by removing any tweets across its platform that included screenshots of its internal tools, and in some cases temporarily suspended the ability of those accounts to tweet further.Another Twitter account — @shinji — also was tweeting out screenshots of Twitter’s internal tools. Minutes before Twitter terminated the @shinji account, it was seen publishing a tweet saying “follow @6,” referring to the account hijacked from Lucky225.Cached copies of @Shinji’s tweets prior to Wednesday’s attack on Twitter are available here and here from the Internet Archive. Those caches show Shinji claims ownership of two OG accounts on Instagram — “j0e” and “dead.”KrebsOnSecurity heard from a source who works in security at one of the largest U.S.-based mobile carriers, who said the “j0e” and “dead” Instagram accounts are tied to a notorious SIM swapper who goes by the nickname “PlugWalkJoe.” Investigators have been tracking PlugWalkJoe because he is thought to have been involved in multiple SIM swapping attacks over the years that preceded high-dollar bitcoin heists.
Archived copies of the @Shinji account on twitter shows one of Joe’s OG Instagram accounts, “Dead.”Now look at the profile image in the other Archive.org index of the @shinji Twitter account (pictured below). It is the same image as the one included in the @Shinji screenshot above from Wednesday in which Joseph/@Shinji was tweeting out pictures of Twitter’s internal tools.
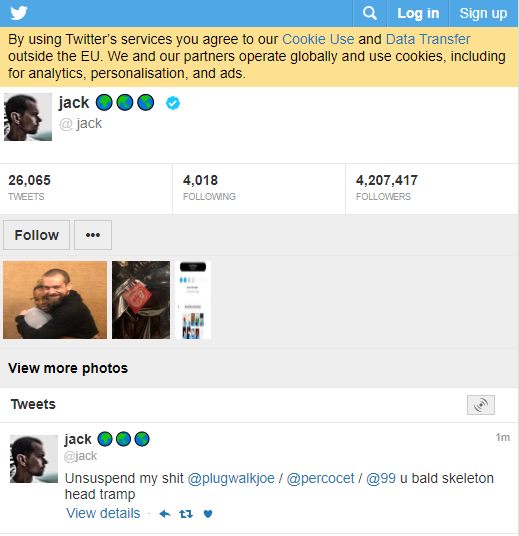
Image: Archive.orgThis individual, the source said, was a key participant in a group of SIM swappers that adopted the nickname “ChucklingSquad,” and was thought to be behind the hijacking of Twitter CEO Jack Dorsey‘s Twitter account last year. As Wired.com recounted, @jack was hijacked after the attackers conducted a SIM swap attack against AT&T, the mobile provider for the phone number tied to Dorsey’s Twitter account.
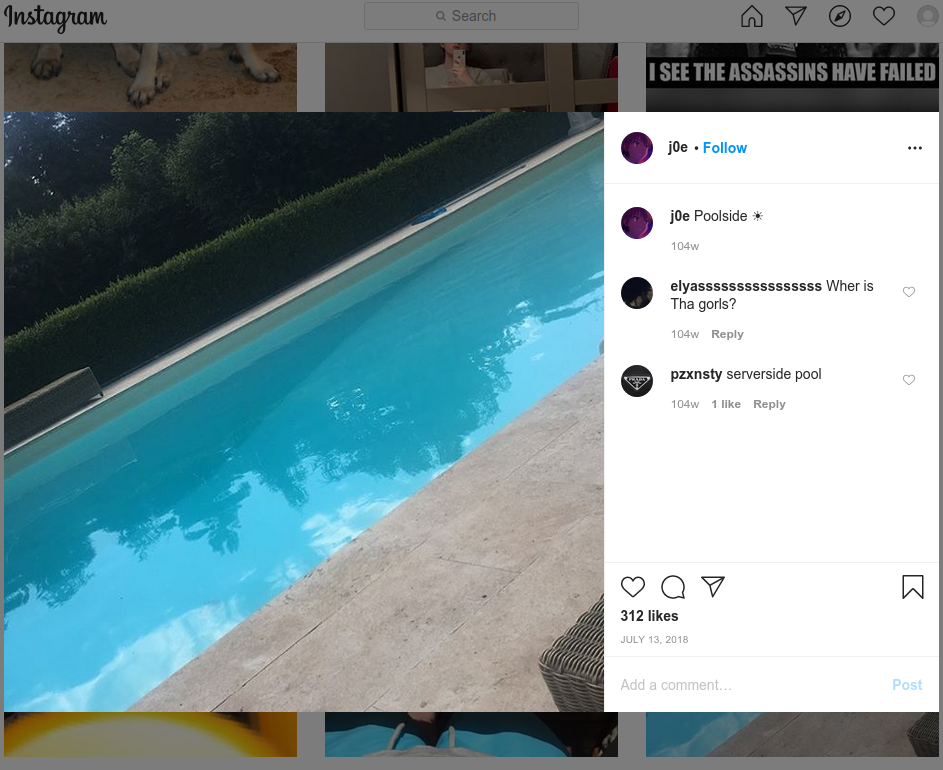
A tweet sent out from Twitter CEO Jack Dorsey’s account while it was hijacked shouted out to PlugWalkJoe and other Chuckling Squad members.The mobile industry security source told KrebsOnSecurity that PlugWalkJoe in real life is a 21-year-old from Liverpool, U.K. named Joseph James Connor. The source said PlugWalkJoe is in Spain where he was attending a university until earlier this year. He added that PlugWalkJoe has been unable to return home on account of travel restrictions due to the COVID-19 pandemic.The mobile industry source said PlugWalkJoe was the subject of an investigation in which a female investigator was hired to strike up a conversation with PlugWalkJoe and convince him to agree to a video chat. The source further explained that a video which they recorded of that chat showed a distinctive swimming pool in the background.According to that same source, the pool pictured on PlugWalkJoe’s Instagram account (instagram.com/j0e) is the same one they saw in their video chat with him.If PlugWalkJoe was in fact pivotal to this Twitter compromise, it’s perhaps fitting that he was identified in part via social engineering. Maybe we should all be grateful the perpetrators of this attack on Twitter did not set their sights on more ambitious aims, such as disrupting an election or the stock market, or attempting to start a war by issuing false, inflammatory tweets from world leaders.Also, it seems clear that this Twitter hack could have let the attackers view the direct messages of anyone on Twitter, information that is difficult to put a price on but which nevertheless would be of great interest to a variety of parties, from nation states to corporate spies and blackmailers.This is a fast-moving story. There were multiple people involved in the Twitter heist. Please stay tuned for further updates. KrebsOnSecurity would like to thank Unit 221B for their assistance in connecting some of the dots in this story.



















0 comments:
Post a Comment