Christopher Moyer reports in Motherboard:
"I never meant for it to get this big, to be honest."On Saturday, February 4, 2017, a self-described "pissed off high school student" in the United Kingdom sat in front of his computer, listening to Bones and Yung Lean, coding a rootkit, a set of software tools that allows an unauthorized user to control a computer system. He got to thinking about recent news reports about printer hacking and shifted gears, instead building a short program in C.
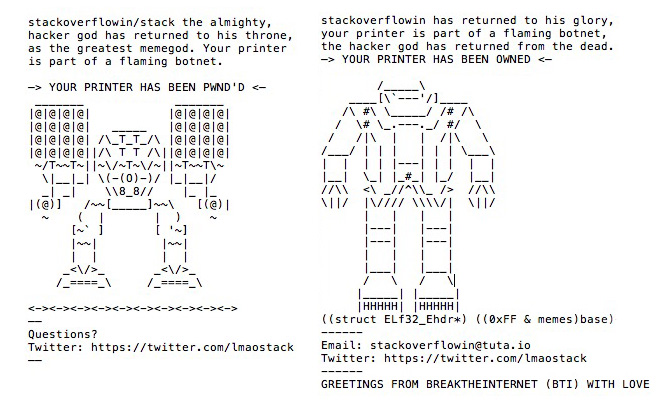
Within hours, roughly 150,000 internet-connected printers across the world began spitting out ASCII art and messages informing their owners that their machines were "part of a flaming botnet." The hacker signed his work as "Stackoverflowin."
Throughout the evening and into Sunday, people across the web reported finding the mysterious printouts. Many of the affected printers were connected to restaurant POS systems, leaving confused employees to find ASCII robots pouring out of their receipt printers.
It has already been a banner year for printer hacking. Internet-connected printers of at least three American universities—Stanford, Vanderbilt, and the University of California and Berkeley—were hijacked and used to print anti-Semitic flyers. In the same week, researchers at Ruhr-University Bochum in Germany published a paper on security vulnerabilities in printers, as well as setting up a wiki to catalogue related exploits. Just days later, Stackoverflowin made his move in an attempt to draw increased attention to the problem.
Intrigued, I contacted Stackoverflowin over Ricochet, an anonymous instant messaging app. We chatted about Internet of Things security, backdoors in Chinese manufactured goods, and his undying distaste for "skids", or script kiddies, unskilled people who use scripts or programs to attack computers but lack the knowledge to write their own.
Motherboard: You've said before that you were doing this to call attention to the security flaw—how'd you do it, and how can end users protect themselves? Stackoverflowin: I did it by sending jobs to printers using the LPD protocol (port 515), IPP (port 631), and raw print jobs on port 9100. Along with this, I used an RCE [remote code execution, an exploit allowing the hacker to run arbitrary code on the target computer] which affected Xerox's web control panels. I could create jobs and use my own PostScript to my liking. People need to take their printer out of the public internet unless it's needed, to be honest. And if it's needed, they should be whitelisting IPs/IP subnets [approving connections from specific IP addresses while blocking all others] or using a VPN to access the local network.
And you automated the process of sending the requests, I take it?Yes, I created a small program in C to do so.
In the printouts you told people their machines were a part of a botnet, even though they actually weren't. Why that choice?It's the first thing that came to my mind, and with growing concerns about IoT security I thought it would be appropriate.Some of the rogue messages Stackoverflowin sent to printers around the world.
The printouts said you "utilised BTI's (break the internet) complex infrastructure, operating on Putin's forehead?"If you're wondering what BTI is, it was a group of a few friends of mine. Lots of forehead jokes go around, mainly involving security researchers, which inspired me about the Putin joke. It was more to stun than anything. People automatically think "lol Rusisa [ sic], w0w."
Why the printers specifically? Did the Ruhr-University Bochum paper or something call it to your attention, or do you just have a general interest in Internet of Things issues?Yeah, I do. I've looked at printers once before (like a few months ago) and poked around, then I came back to it when I saw a few articles about them. I've been trying to clean up the IoT mess since like early 2015. I've run honeypots on the scale of fingerprinting every major IoT bot.
Stuff got real interesting when [the IoT malware] Mirai came around though, and people started to really notice the problem. But people were already ahead of the game when it came to threat intelligence and the whole thing became a bit corporate as everyone was now interested in it, so I didn't bother. In terms of this type of IoT, I'm not sure if it's the type of IoT that spurts into a consumer's mind when they think of IoT. It's moreso DVRs/routers/printers in the case of the IoT security problem. I think the media blows it out of proportion a bit. People are thinking their toasters and shit are getting rooted on a daily basis.
Right, that someone's going to mess with your smart fridge and your milk will go bad. It's got a massive potential for fucking up. Most of the devices that are used in attacks are sold by one company but manufactured by another—often by sketchy Chinese developers. No racism intended here. Their code is shocking and there are multiple backdoors in a load of internet enabled devices.
"I never meant for it to get this big, to be honest."
Tell me about the actual moment of the hack. I'm trying to picture the scene. It's Saturday and what, you're bored at the desk with a coffee and decide to pull something off?
I never meant for it to get this big, to be honest. When it came back that like 158,000 hosts were replying, I was kinda stunned. I didn't think it'd get this much attention either. Yes, it was Saturday and I was sitting, listening to Yung Lean and drinking a coffee with two sugars. I think I was working on a sandbox to brush up my Linux kernel programming skills—thought it'd be interesting as I'd mucked about with user mode stuff for a while and was getting bored of it. Or that night I was working on my LD_PRELOAD kit [a type of rootkit]. It was just a night I was bored to be honest, doing random shit.
You signed the name Michael Jensch on some of the printouts, and your Twitter account says you're a 23-year-old researcher in Germany. But you've told others you're a high school student in the UK.
Oh, that's my friend. He kinda asked me to do it. And yeah, I'm from the UK. I'm a high school student. A pissed off high school student who fucked his future in computing science.
I doubt it sincerely, since nobody knows who you are anyway.Nah, just in real life. I did not get the grades I wanted. I guess I'll be doing more of this shit for the rest of my life.
What do you think has kept you from getting the grades you want? What would your teachers think if they knew what you got up to over the weekend?An obsession with programming. I was doing about 14 hours a day at that time. So, yeah, pretty much fucked my grades. One problem I have is that I'm not noticed at all for my skills. Everyone I know who is this age and has the skillset I have are either blackhat or legit depressed. There's nothing for us at this age.
What would the dream job be?I hope to work for myself one day or another and do some type of startup. Most likely a head embedded systems programmer or even a security consultant possibly would be my dream job, something security and software development related.
Do you think university's in the cards?Many confused owners of affected printers took their questions to the Internet, like this one from the Hewlett-Packard support forums.
Nah, I didn't get the grades to do what I want. Now I'll have to do some terrible course that I don't want to do. Well, it's still uni, just far from what I want to do. I honestly wish there was something for our age with this kind of skill. There's legit nothing, dude. In France they have coding colleges and shit (such as 42.fr, Epitech, etc).
You don't have computer science programs in the UK?
No, yeah, we do, but they're terrible. For example, my class at this moment, which is "computer science"—not one my classmates can program or have any enthusiasm toward the subject. It's basically an exercise of who can copy out of the book the fastest in their case. And all find it quite challenging. Hackathons; conferences; CTFs [Capture the Flags]; that kind of stuff, more stuff in schools—there's nothing. My skills in terms of programming really aren't noticed either, or anything else regarding computer for that matter. And yeah, I'm just way ahead of my peers when it comes to it.
I get it. In my experience the feeling you're describing isn't uncommon among hackers—it's that natural curiosity and desire to be challenged that gets you to where you are, and not everyone shares it. What about starting the sort of thing you'd be into yourself?I don't know enough people. I don't talk about any of this stuff with my friends. Nobody is interested in it. I've had my fair deal of shit from teachers when it comes to computing, too.
Like?Like reporting vulnerabilities responsibly then getting in a load of shit for it. It was to do with another organization though, but the school used it. And I got in LOT of shit for that. Even though I did the usual private disclosure, PoC [Proof of Concept], etc, all in private. I did the right thing but got shit on for it and they told me to "not go prodding around," even though that system had a lot of sensitive information about students and the like. That's just one of the examples, though. There's a load of shit. There's no way out of this.
And if you did have other outlets to satisfy your skill and curiosity, do you think you'd still be sending rogue print requests?Nah, I wouldn't do it again. Or would I still do it? I don't really know. More personality based than anything. I think this will be the last time I'll do it. I want to move on from this type of stuff. It's received a lot of attention for the wrong reasons, too. To other high school hackers, I'd say surround yourself with like-minded people who share the same interests. It's the best way to grow as a person when it comes to this type of stuff as it can be so niche. Don't be arrogant about it. People hate that sort of stuff, but it's done easily enough. Don't do stupid shit, either. It never ends well. That includes exposing devices to the internet that don't need to be.




















78 comments:
Hello, I am a developer and I got an website for development purpose so I need your help to develop it. This website is related to essay service so please suggest me to develop and design it.
Sorry I don't say anything about this because I have no knowledge about this. I want to know deep about this. Gustavo Woltmann
I was exactly searching for this . Thanks for such post and please keep it up
Bridgerton Simon Bassett Tailcoat
If we are going to talk about murals, it is a harsh reality that there are people who do not appreciate artworks like this. I fell bad, but there is less that I can do; I want them to realize that murals are beautiful and worth appreciating. But I simply don't know where to start. Sometimes, Tony Montana Jacket I think of writing as my way to influence people to appraiser things that should be appreciated. I don't know if that is going to be effective, but I want to give it a try.
Ensure the lethargic music you decide to play before resigning to bed must have a delicate, consistent and ordinary musicality. I have just read e review and got many information as this customary Top Gun Jacket and steady beat causes you to feel loose and facilitate your feelings of anxiety, in this manner making it simpler for you to nod off.
This is the kind of manua Mens Cotton Jacket From Godzilla Vs Kong that needs to be given and not the random misinformation that's at the other blogs. Appreciate your sharing this best posting.
I really enjoyed this site. This is such a Great Godzilla Vs Kong Cotton Jacket resource that you are providing and you give it away for free. It gives in depth information
I really enjoyed reading your articles. It looks like you’ve spent a lot of time and effort on your blog.
Justin Bieber Pink Puffer Jacket
Continuous examinations have shown that 77% workforce acknowledge that modified learning is fundamental for individual and master new development. The best online mechanized promoting course helps you with learning at your speed and gives altered educating to ensure that you grasp advanced thoughts from industry trained professionals. Beside learning at unimportant cost, you get a significantly regarded accreditation and position help to dispatch your calling.
Thank you for this interesting news. It proves that what makes an IoT device usable — the ability to remotely and centrally manage it from anywhere in the world — is also the biggest security threat. As noted in Palo Alto Networks' 2020 Unit 42 IoT Threat Report, 98% of IoT device traffic is unencrypted and transmitted in clear text over the Internet. I think that's why this guy managed to carry out such an attack. By the way, on YouTube you can find a dozen videos in which experienced programmers talk about IoT and the Internet of Things, personally I managed to find a couple of dozen of these videos and almost all of them had more than 80 thousand views! I am sure that in order to achieve such impressive views, their authors have repeatedly resorted to using the services of https://soclikes.com/ for quick and inexpensive cheating of the number of views.
Thanks for this great. I am wondering if you were planning of publishing similar articles to this one. .Keep up the excellent posts! Black Leather Jacket Mens
Thanks for the nice blog. It was very useful for me. I'm happy I found this blog. Punisher Vest
This is such a wonderful post. I have learned new things here. Your writing style is great. keep up the good work Celebjacket
I have read your blog; it’s very informative and helpful for me. I admire the valuable information you provide in your blog. Thank you for posting it. Peaky Blinders Outerwear
I think this is an informative post and it is very beneficial and knowledgeable. Therefore, I would like to thank you for the endeavors that you have made in writing this article. All the content is absolutely well-researched
cinema hd v2
Thank you for this interesting news. It proves that what makes an IoT device usable — the ability to remotely and centrally manage it from anywhere in the world — is also the biggest security threat. Don't you think it's worth make a video on this article and post it on Youtube? There a large audience of users will be able to see it. You can also always use the services of https://viplikes.net/buy-youtube-views in order to wind up the number of views.
Excellent post it is full of knowledge Dove Cameron mal studded Halloween Leather jacket and inspiring content good work. keep it up.
Thanks for sharing such an amazing post. It was really helpful. Keep sharing more content.
find so many useful info here in the post, we need work out more techniques in this regard, thanks for sharing.tom hiddleston leather jacket
If you would like to improve your knowledge only keep visiting this web site and be updated with the newest gossip posted here.Our new website has been launched and we are offering some exciting prices. Check it out now.
mens satin jackets
Hello, thank you for sharing your article with us, and I truly value your information, which I really appreciate, and I would visit your website again.brown bomber jacket
Check out our latest products at Real Jackets. The real leather jacket store, men, women, celebrity, halloween and gaming jackets. Explore more to get your favourite product for your wardrobe.
battletech bomber jacket
Thanks for the post. I’ll certainly comeback.Squid Game Green Jacket
Jason Sudeikis jacket his wardrobe collection is across the board as he shows off Ted Lasso Jacket
cinema hd official apk
cinema hd apk
how to install cinema hd apk on firestick
download cinema hd on iphone
cinema hd not showing yellow links
download cinema apk
This is the one of the most important information for me. And I am feeling glad reading your article. The article is really excellent?
Natalie Bauer Pink Vest
Goodness! Much obliged to you! I constantly needed to compose on my site something to that effect. Would i be able to incorporate a part of your post to my site.Men Bomber Jacket
Good day! This post couldn't be composed any better! Perusing this post helps me to remember my old fashioned flat mate! He generally continued discussing this. I will advance this review to him. Almost certain he will have a decent perused. Much obliged for sharing!Aviator Jacket
Africa News Publisher Things that you have covered in this article or blog is really wonderful.
Thanks for the best share and i loved it, 192.168.o.1
Your post was amazing. I love it to recommend Leather Store to the users. Where they can crawl Exciting Products Super Star Jackets Platform is providing 100% Geniune Leather Products All products are available in Feasible Prices The best seller Leather Jackets Direct is offering amazing Leather Jackets to its customers. You can Click Here to get exciting Leather Products OffersBrown Leather Jacket
The 355 Fan Bingbing Black Cotton Jacket is upcoming trending Jacket and everyone wants to get this product and we know this product is being sold on various platform bus we have some special offer for you this offer is being given for Christmas with 30% discount don't be late
our customers enjoy huge range of genuine and reliable electronics, appliances, LED TVs, mobiles and accessories at best prices, delivered right at their doorstep. There are multiple categories for our customers to explore.
Refrigerator price in Pakistan
So let him try the game at https://techgara.com/poppy-playtime to see if he can attack?
I am so happy to come across.Film Jackets
enjoy your website, the trust may provide you a more heavenly blog,Bridgerton Lord Featherington Green Tailcoat leather jacket Thank you very much for this post, and please keep it up. has made a good presence here to gather all of the data content and data in one place.
Very interesting article. Brown Gap Hoodie I'm looking forward to reading more. Thank you for your comment.
Laser printing is an electrostatic digital printing process. It produces high-quality text and graphics (and moderate-quality photographs) by repeatedly passing a laser beam back and forth over a negatively-charged cylinder called a "drum" to define a differentially-charged image.
3D Printer Filaments
The narrative of "The Abbotts," who are dealing with the disappearance of their daughter-in-law as the adjacent Tylors make a bid for their ranch land, is told in the American supernatural mystery thriller streaming television series " Rhett Abbott Black Leather Vest ." Lewis Pullman plays Rhett Abbott and looks like a piece of eye candy in the Outer Range Rhett Abbott Leather Vest.
The inspiration for this coat came from the American criminal thriller and action film No Time To Die James Bond Duster Coat , in which veteran actor Daniel Craig donned this coat while playing James Bond. The outside of this James Bond duster coat is made of high and premium grade corduroy material.
Thank you for sharing such useful information that is sometimes difficult to come by. You did a fantastic job. Your website is extremely user-friendly, and the material is fantastic. Both your website and essay are fantastic. I'm a blogger that focuses on fashion and leisure. You can see examples of my work on this website.
This article wowed me; this website has always provided me with good news. Thank you for such an excellent topic; Matt Smith Trench Coat I meet them more frequently than I visit this site.
I am so happy to come across this piece of write up, very much advanced my understanding to the next top level. Great job and continue to do same.
I really enjoyed this site. This is such a Great resource that you are providing and you give it away for free. It gives in depth information. Thanks for this valuable information.
I never stop myself to mention some thing about it. You’re doing a remarkable process. Hold it up Star Wars Andor Outfits
The information provided by you is really very good and helpful for me. Keep sharing good information USA Jacket
This classy Me Time 2022 Mark Wahlberg Blue Tracksuit for men is available in blue with straight bands of the same colours running down the length of the trouser sleeves and diagonal bands on the chest of the track jacket.
Your Article Is Well Written And Simple To Understand. You Make Excellent Points. Thanks For The Blog…..
This post has a lot of insightful and useful information. I want to express my gratitude to you for your efforts in authoring this essay. Here are a few texts about How does Morse Code Work. Please visit translate morse code and let me know what you think.
I love how you broke down a complex topic into easily understandable points. The color blind test online was a fun and educational way to test my color perception abilities.
Your writing style is engaging and kept me hooked until the end. I was surprised by how well I did on the color blind test online, it boosted my confidence in identifying colors.
This is really an amazing article.Thanks a lot for sharing a piece of wonderful information. keep it up posting.
Hells Angels Vest
Your article takes readers on a journey of discovery. The way you explore different facets of the topic enriches the narrative.I highly recommend click faster in Minecraft to anyone who wants to level up their clicking abilities. It's an enjoyable and practical tool.
Wow, this video was eye-opening! It's crazy to think that a bored teen could expose the vulnerability of the Internet of Things on such a massive scale. This serves as a stark reminder of the importance of cybersecurity in our increasingly connected world. Kudos to the young hacker for shedding light on this issue and sparking a much-needed conversation!
https://brown-leatherjackets.com/products/shearling-brown-leather-jacket-women
Wow, this story is a wake-up call! It's crazy how a bored teen exposed the vulnerability of the Internet of Things. We all need to take cybersecurity seriously.
https://brown-leatherjackets.com/blogs/news/top-10-halloween-costume
Lowdown" typically refers to the most up-to-date and essential information or knowledge about a specific topic, situation, or event. It can also describe a straightforward and trucking accidents attorneys succinct summary or briefing on a particular matter. The term is often used informally to convey the latest insights or key details.
The tale of a bored teen hacking 150,000 printers highlights the alarming vulnerability within the Internet of Things (IoT). This incident sheds light on the pressing need for robust cybersecurity measures in connected devices. The teen's exploit serves as a wake-up call, underscoring the potential risks when IoT security is neglected. It emphasizes the importance of educating both users and manufacturers about the potential consequences of lax cybersecurity practices. The story underscores the urgency for a proactive approach in addressing IoT vulnerabilities to safeguard against unauthorized access and potential cyber threats.
divorcio en las leyes de nueva jersey
reckless driving virginia 85 mph
The article highlights the importance of cybersecurity in the Internet of Things (IoT) by revealing a teen hacking 150,000 printers. The story highlights the potential consequences of unchecked vulnerabilities and emphasizes the need for increased awareness and security measures. The article also highlights the ethical considerations surrounding hacking and the role of individuals, organizations, and policymakers in addressing IoT vulnerabilities. The real-world impact of the hacking on 150,000 printers highlights the scale of cyber threats in the IoT landscape.
The story of a disinterested teenager breaking into 150,000 printers exposes the glaring weakness in the Internet of Things (IoT). This bold exploit highlights the potential devastation that may occur when IoT security is disregarded, and it makes a gripping cautionary story. The need for strong cybersecurity measures in an increasingly linked world is made clear by the teen's inventiveness. The event highlights the wider ramifications of unaddressed technological vulnerabilities and calls for a group effort to strengthen digital infrastructure. It is a wake-up call that makes one consider the fine line that must be drawn between technological advancement and the need to protect against malevolent exploitation.
fatal motorcycle accident in virginia
You have a remarkable ability to find silver linings in every situation, and it's truly inspiring.CPS TestThe Click Speed Test on CPS Test is a fun way to challenge yourself and improve your clicking speed!
Thank you for inspiring us to savor each moment and embrace the joy of living. Clicker Testhas revolutionized the way I interact with websites, enabling seamless navigation and interaction.
The documentary explores a bored teenager who hacks 150,000 printers to print a message. It offers a light-hearted look at teenage ingenuity and captures the teenager's thought process. However, it raises questions about cybersecurity vulnerabilities and the lengths teens might go to when feeling restless. The documentary also explores the consequences of the hack for the teenager, discusses cybersecurity awareness, and offers solutions to teenage boredom.
estate and gift taxes lawyer
A bored teenager took advantage of the weak cybersecurity around printers to boldly and alarmingly demonstrate the Internet of Things' (IoT) weakness by breaking into 150,000 of these devices. This action acts as a wake-up call, emphasizing how urgently IoT security measures must be strengthened. It emphasizes the possible dangers that, if ignored, connected devices may cause. Because of this occurrence, manufacturers and customers should place a higher priority on cybersecurity and make sure that Internet of Things devices are sufficiently shielded from harmful attacks. It serves as a sobering reminder of the constant threat that exists in our globally connected digital world.
virginia reckless driving fairfax
Your blog fills me with hope and positivity, reminding me that there's always a silver lining! The CoreBall version you mentioned seems intriguing, similar to what I've seen on CoolMathGames.
A lady’s touch on the classic motorcycle jacket design makes this Women’s Black Faux Leather Jacket one of a kind, purely stylish, and an ideal addition to any woman’s closet. Black is sleek, timeless, and goes well with just about everything from gowns to tops and jeans. Whether you’re looking for a night out with friends or running errands, oh boy, this Women’s Black Faux Leather Jacket definitely won’t pass unnoticed.
Thanks for the inspiration, I’m feeling motivated! Visit this useful website mental age for more great content.The mental age test gave me a lot to think about. While it’s just for fun, it made me more aware of how my habits align with different age groups.
Thank you for your amazing content! It has genuinely motivated me to pursue blogging.
Yellowstone S05 Luke Grimes Brown Jacket
This article brilliantly highlights the shocking vulnerability of IoT devices through a captivating story. Just like the thrilling unpredictability of Yellowstone, it reminds us that danger often lurks where we least expect it.
This is one of the best articles I’ve read on this subject. Thank you for putting it together! Visit this profile canuckle game for more informative content. The combination of word puzzle and Canadian trivia in Canuckle is just perfect. It’s not only fun but also a great way to learn new words!
How A Bored Teen Hacked 150,000 Printers To Show the Internet of Things' Vulnerability offers a fascinating and cautionary tale about the security risks of interconnected devices. The review explores how a teenager, with little more than curiosity and technical know-how, exploited vulnerabilities in the Internet of Things (IoT) by hacking a massive number of printers. This bold act not only demonstrated the potential for widespread disruption but also highlighted the often-overlooked weaknesses in IoT devices, which are frequently left unsecured.
Traffic Lawyer Harrisonburg VA
TheLowdownBlog provides insightful reviews and discussions on a variety of topics, including lifestyle, entertainment, and culture. It offers readers a fresh perspective on current trends, helping them stay informed and engaged Traffic Lawyer King George VA
This article is so well-written and insightful. I’ve bookmarked it for future reference. Visit thi site reaction test for more informative content.This reaction time test is so well-designed! It’s easy to use and gives instant feedback, which makes it incredibly rewarding. Great job.
The legal ramifications of dissolving a marriage, such as property distribution, child custody, and other crucial issues, are handled by divorce attorneys. When needed, they will represent your interests in court or try to reach just settlements between spouses. Having a knowledgeable attorney at your side may be quite beneficial, especially considering the emotional and legal difficulties that come with divorce. Our Manassas divorce lawyers are available to assist you if you need professional advice. Get in touch with us now to find out more.
How a bored teen hacked 150,000 printers to show the Internet of Things' vulnerability explores a remarkable story highlighting the risks associated with connected devices. This incident showcases how a young individual exploited security flaws in the Internet of Things to demonstrate how vulnerable these devices can be to cyberattacks.loudoun county criminal court records provide public access to legal documents and case information related to criminal proceedings within Loudoun County. These records include details about arrests, charges, court dates, case outcomes, and other important legal proceedings.
Maria Clara combines historical heritage with contemporary design to provide a delightful and genuine experience. The menu features delicious dishes prepared with high-quality, fresh ingredients, and the atmosphere is cozy and welcoming. It's the ideal place for anyone looking for a special dinner experience because of the attentive service. Strongly advised!The general law in the USA is a complex and evolving system rooted in both federal and state jurisdictions. It encompasses a wide range of legal principles, including constitutional, statutory, and case law. The system aims to balance individual rights with public order and safety. While it provides a framework for justice and legal processes, its complexity and variation across states can pose challenges. The ongoing development of laws reflects societal changes and strives to address contemporary issues, maintaining a dynamic legal landscape.
Dui Lawyer Smyth VA
Post a Comment